Vault Configuration
This document explains how to enable and configure the HashiCorp or Azure Vault in TimeBase settings.
HashiCorp Vault Configuration
The HashiCorp Vault is a tool for securely managing secrets, such as API keys and passwords.
tip
Ensure that HashiCorp Vault is correctly installed and accessible at the specified Vault URI before proceeding with the configuration.
Environment Variables
To configure the HashiCorp Vault using environment variables:
- Set the vault address using
VAULT_ADDR=<vault uri>. - Set the vault access token using one the following options:
VAULT_TOKEN=<vault access token>- Place the token in the
.vault-tokenfile in theuser.homedirectory.
note
Token path mangling is not supported for VAULT_TOKEN and .vault-token.
Optional Properties
- SSL certificate path:
VAULT_SSL_CERT=<path to cert pem file> - SSL verification:
VAULT_SSL_VERIFY=<true|false>(default=true) - Open timeout:
VAULT_OPEN_TIMEOUT=<timeout sec> - Read timeout:
VAULT_READ_TIMEOUT=<timeout sec>
Java System Properties
To configure the HashiCorp Vault using java system properties:
- Set the vault address using
-Dvault.addr=<vault uri>. - Set the vault access token using
-Dvault.token=<vault access token>.
Optional Properties
- SSL certificate path:
-Dvault.ssl.cert=<path to cert pem file> - SSL verification:
-Dvault.ssl.verify=<true|false> - Open timeout:
-Dvault.open.timeout=<timeout sec> - Read timeout:
-Dvault.read.timeout=<timeout sec> - Engine version:
-Dvault.engine.version=<engine version>(default=2)
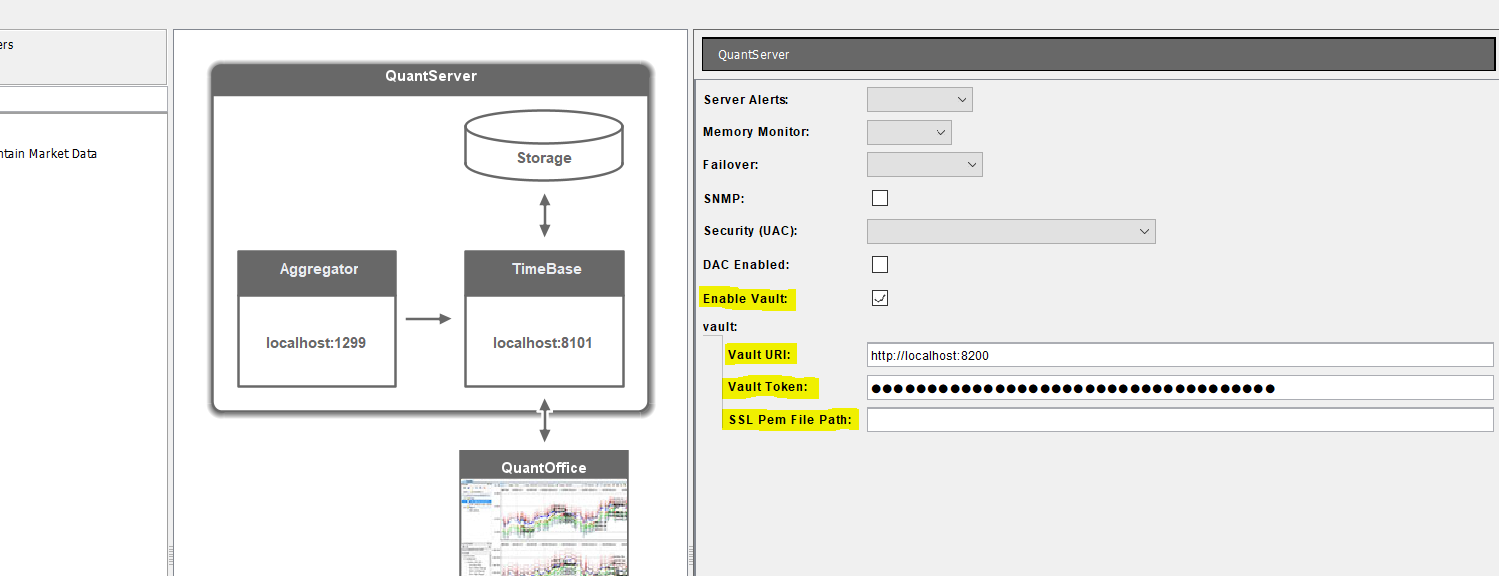
QSArchitect
Vault settings can be configured in the Aggregator's admin.properties or QSArchitect's configuration file as follows:
QuantServer.enableVault=true
QuantServer.vault.addr=http\://localhost:8200
QuantServer.vault.token=EV6af9...encoded token value
QuantServer.vault.sslCert=
To configure in QSArchitect:
Azure Key Vault Configuration
Environment Variables
To configure the Azure Key Vault using environment variables:
- Set vault provider type
VAULT_PROVIDER=AZURE. - Set the vault address using
VAULT_ADDR=<vault uri>. - Configure the following Azure Key Vault credentials if not configured in system:
- Set
AZURE_CLIENT_ID=<client id>. - Set
AZURE_CLIENT_SECRET=<client secret>. - Set
AZURE_TENANT_ID=<tenant id>.
- Set
Java System Properties
To configure the Azure Key Vault using java system properties:
- Set the vault provider type using
-Dvault.provider=AZURE. - Set the vault address using
-Dvault.addr=<vault uri>. - Configure the following Azure Key Vault credentials if not configured in system:
- Set
-Dvault.azure.clientId=<client-id>. - Set
-Dvault.azure.clientSecret=<client-secret>. - Set
-Dvault.azure.tenantId=<tenant-id>.
- Set
QSArchitect
Vault settings can be configured in admin.properties as follows:
QuantServer.enableVault=true
QuantServer.vault.provider=AZURE
QuantServer.vault.addr=https\://<key-store-name>.vault.azure.net/
QuantServer.vault.clientId=<client id>
QuantServer.vault.clientSecret=<EVfffae...encoded secret value> # client secret is mangle encoded
QuantServer.vault.tenantId=<tenant id>
Defining Secrets
To securely reference secrets stored in the vault within your application configurations, use the following template syntax: vault:<path>/<name>.
For example, if there is a secret named my_secret located at /secret/my/sub/dir in the admin.properties file, specify it in the configuration as:
QuantServer.security.oauth2Login.secret=vault\:/secret/my/sub/dir/my_secret